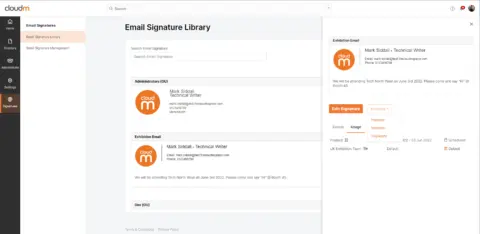
Design, deploy and automate email signatures for Google Workspace
Manage your organization’s signatures from one user-friendly place with dynamic user groups and smart automation features.
Request a demo




Save time and boost productivity with automated email signatures
Swiftly create and deploy email signatures, automatically assign them to departments or dynamic groups, and streamline onboarding/offboarding with smart automation for new team members.
.
Key Features
Maximize sales and marketing impact with strategic email signature management
Elevate sales and marketing campaigns with scheduled custom email signatures featuring banner announcements and seasonal content.
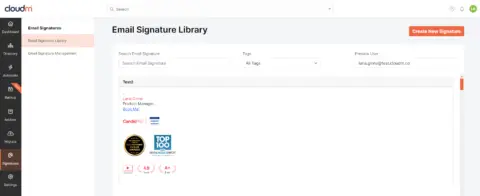
Enhanced security with direct access
CloudM Email Signatures directly apply signatures within user settings, enhancing data security by eliminating the need to route signatures through 3rd party external servers.
"Email signature changes run seamlessly in the background and can be made without involving every member of staff in the process. Alleviating pressure in SaaS management has lifted a huge burden so the team can focus on what they do best."
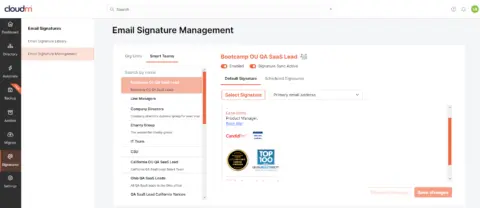
Consistent email signatures in four simple step
Let your team focus on more important tasks while reducing the risk of mistakes by automating data retention policies and license reassignment as part of your offboarding workflow.
Choose what’s included
Make it your own
Test your template
Roll it out
All signatures are centrally managed and automatically updated with the click of a button. Seasonal sales and marketing messages, events promotions and more are centrally managed in CloudM with no need for internal communication or manual updates across a widespread workforce. It really is a useful tool that has improved our processes and saved me so much valuable time.
Book a call with our email signature specialists today.







